July 28, 2022, 11:52 p.m.
Retrieving Superadmin Password on ZTE MF286RA using CP2102
Originally Published on July 18, 2022
For a video guide, please refer to:
This guide is for PC/Laptop users only!
Requirements:
- CP2102 USB UART/Serial
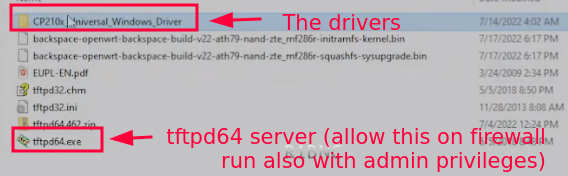
- Download CP2102 Windows Driver Installer
- Jumper cables (Female to Female)
- Soldering iron and Solder
- Male headers (optional)
- Download PuTTY application
Steps:
1. Open up your ZTE MF286RA (Warranty will now be void!). There are no screws to remove, all are plastic clips.
2. Look for the unpopulated UART port and solder it with jumper cable or male headers (if you want the wires be removable).
The end product should look like this:

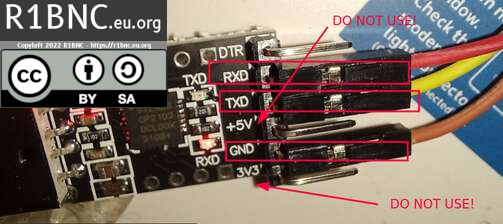
3. Plug in the jumper wires to the CP2102 as shown on the photo below. Never connect 5V or 3.3V on the CP2102 as it will damage your ZTE router.
4. Plug in the USB CP2102 and install the driver (the download link is shown above).
Open up Computer Management and navigate to Device Manager, you should now see the COM port section.
Start up PuTTY and match the configuration below, COM port may vary.
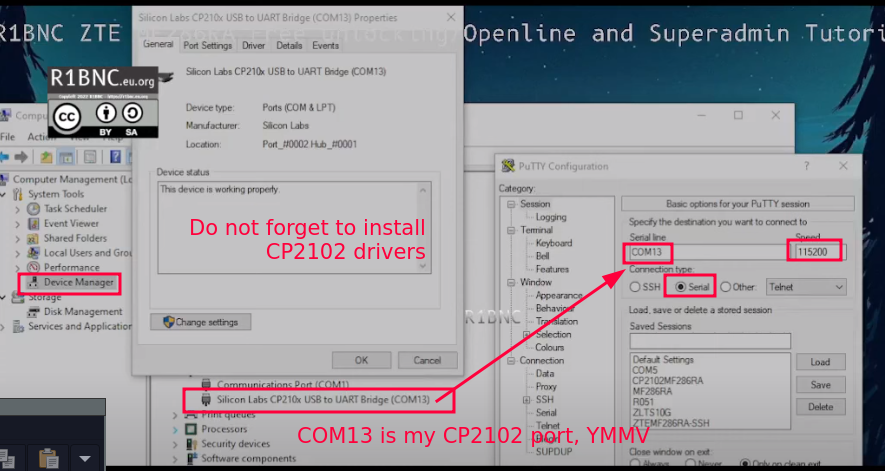
5. Click Open on PuTTY and you should now be on the ZTE MF286RA Shell. Execute the following to get the super admin password.
nv get web_password1|base64 -d
This should give you random password for the superadmin account, if you bought the ZTE boxed and sealed this should give you the permanent superadmin password.
If you want to get the tech account password do:
nv get web_password3|base64 -d
For the globe admin password (lowest access level):
nv get web_password2|base64 -d
Sample output:
BusyBox v1.19.4 (2021-06-08 22:33:52 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
MM NM MMMMMMM M M
$MMMMM MMMMM MMMMMMMMMMM MMM MMM
MMMMMMMM MM MMMMM. MMMMM:MMMMMM: MMMM MMMMM
MMMM= MMMMMM MMM MMMM MMMMM MMMM MMMMMM MMMM MMMMM'
MMMM= MMMMM MMMM MM MMMMM MMMM MMMM MMMMNMMMMM
MMMM= MMMM MMMMM MMMMM MMMM MMMM MMMMMMMM
MMMM= MMMM MMMMMM MMMMM MMMM MMMM MMMMMMMMM
MMMM= MMMM MMMMM, NMMMMMMMM MMMM MMMM MMMMMMMMMMM
MMMM= MMMM MMMMMM MMMMMMMM MMMM MMMM MMMM MMMMMM
MMMM= MMMM MM MMMM MMMM MMMM MMMM MMMM MMMM
MMMM$ ,MMMMM MMMMM MMMM MMM MMMM MMMMM MMMM MMMM
MMMMMMM: MMMMMMM M MMMMMMMMMMMM MMMMMMM MMMMMMM
MMMMMM MMMMN M MMMMMMMMM MMMM MMMM
MMMM M MMMMMMM M M
M
---------------------------------------------------------------
For those about to rock... (QCA9558.LN, unknown)
---------------------------------------------------------------
admin@(none):~# nv get web_password1|base64 -d
6UJXXXXXXXXXXXXXXX
admin@(none):~# nv get web_password3|base64 -d
tech@XXXX
admin@(none):~# nv get web_password2|base64 -d
Globe@123AB
Full credits to R1BNC and Backspace Team (Discord)
https://ganknow.com/r1bnc/donate
Except where otherwise noted, this work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License (http://creativecommons.org/licenses/by-nc-sa/4.0/).